New Framework Enhances AI Decision-Making in Disaster Response Scenarios
In emergency situations, every second counts. First responders must make rapid decisions about how best to allocate limited resources, often in the face of...
New AI System Predicts Crowd Dynamics to Prevent Safety Risks
Researchers at KAIST have developed an advanced artificial intelligence system capable of predicting crowd movements with far greater accuracy than existing methods. Unlike traditional...
New Police Unit to Monitor Social Media to Prevent Violent Protests
In an effort to better manage public safety threats, the UK government has introduced a new police unit tasked with monitoring social media for...
Live Facial Recognition to Be Deployed at a Large Public Event...
This year’s Notting Hill Carnival in London will see the introduction of live facial recognition (LFR) technology as part of a broader effort by...
MIT Develops Robot to Assist in Search and Rescue Missions
Researchers at the Massachusetts Institute of Technology (MIT) and the University of Notre Dame have developed a robot designed to navigate disaster sites and...
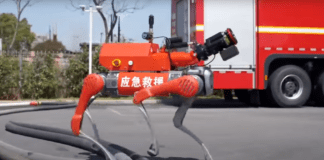
The Robots That Fight Fires
Renowned Chinese robotics company Unitree has introduced its latest innovation in firefighting technology: a new line of quadruped robots designed for fire rescue operations....
Composite Metal Foam: The Future of Ballistic Armor and Heat Insulation
A revolutionary new material, Composite Metal Foam (CMF), is poised to transform various industries, from aerospace to military and even transportation. After years of...
New AI System Detects Damage in Buildings and Enhances Infrastructure Safety
The deterioration and collapse of aging infrastructure is a pressing concern worldwide. Now, researchers at Michigan State University (MSU) have developed an innovative "deploy-and-forget"...
Safer City, Less Privacy? Drone Usage for Emergency Response Sparks Criticism
The New York Police Department (NYPD) has ramped up the use of drones for emergency response, introducing a new level of aerial surveillance over...
Innovative Navigation System Enhances Autonomous Movement in Robotic Dogs
User-friendly robotic technology has just been upgraded with the introduction of a new "One-Touch" navigation feature for quadrupedal robots. This advancement, unveiled by China’s...
This is How AI Technology Amplifies Organized Crime Threats
In a recent report, Europol has raised alarm over the growing use of artificial intelligence (AI) by organized criminal groups, warning that technology is...
Researchers Develop Cost-Effective Drone Systems for Indoor Search and Rescue
In the world of search and rescue, time is critical, and efficiency can save lives—especially in dangerous indoor environments like collapsed buildings. The latest...
Innovative Bio-Hybrid Drone Can Navigate Using Odor
In a recent innovation, Japanese researchers have developed a bio-hybrid drone that merges silkworm moth antennae with robotic technology to improve odor detection and...
Sanctions Imposed on Neo-Nazi Terror Telegram Group
The Australian government has taken a step in combating extremist hate networks by imposing financial sanctions on the neo-Nazi online group known as the...
Cybercriminals Exploit LA Wildfires with Sophisticated Scams
As the devastating wildfires continue to wreak havoc in Los Angeles, cybercriminals are seizing the opportunity to exploit the chaos, targeting both victims and...
Liquid360 – Transforming Surveillance with Augmented Reality
In a country frequently targeted by terror attacks, public safety is a top concern, and effective surveillance plays a crucial role. For this reason,...
New Helicopter Operating System Allows Unmanned Operation
Skyryse, a leader in aviation technology, has teamed up with the U.S. Army to introduce cutting-edge advancements to helicopter operations, particularly enhancing the fleet's...
Incorporating Security Technologies in Critical Infrastructure Structural Systems, Public Buildings and...
Incorporating Security Technologies in Critical Infrastructure Structural Systems, Public Buildings and Real Estate
Written by Or Shalom
In the construction world, security has become a central...
LiDAR Robot to Be Used for Disaster Response and Military Scenarios
In disaster response scenarios, emergency services often face the challenge of assessing dangerous environments without putting themselves at risk. To address this, the Fraunhofer...
The High-Energy Density Battery for Aerial Drones
In a drone technology advancement, Chinese scientists have successfully integrated a high-energy density lithium battery into a composite-wing aerial drone, significantly enhancing its performance....
China Introduces Facial Recognition Police Robots Equipped with Tear Gas
Stepping towards integrating robotics into law enforcement, Chinese authorities have begun testing an autonomous spherical robot, the RT-G, developed by the local robotics company...
The World’s First 100% Electric Patrol Boat
Marine electric vehicle technology leader Voltari has launched its latest innovation, the Patrol 26 RIB, an all-electric patrol boat designed for military, government, and...