RACER – A New 12-Ton Autonomous Ground Vehicle
DARPA has announced that its RACER program (Robotic Autonomy in Complex Environments with Resiliency) recently passed an important milestone by testing its bigger and...
What To Expect – Rising Trends In Security For 2023
According to HID Global, an expert in trusted identity and physical security solutions, these following trends will impact the security and identity industry.
Continuing...
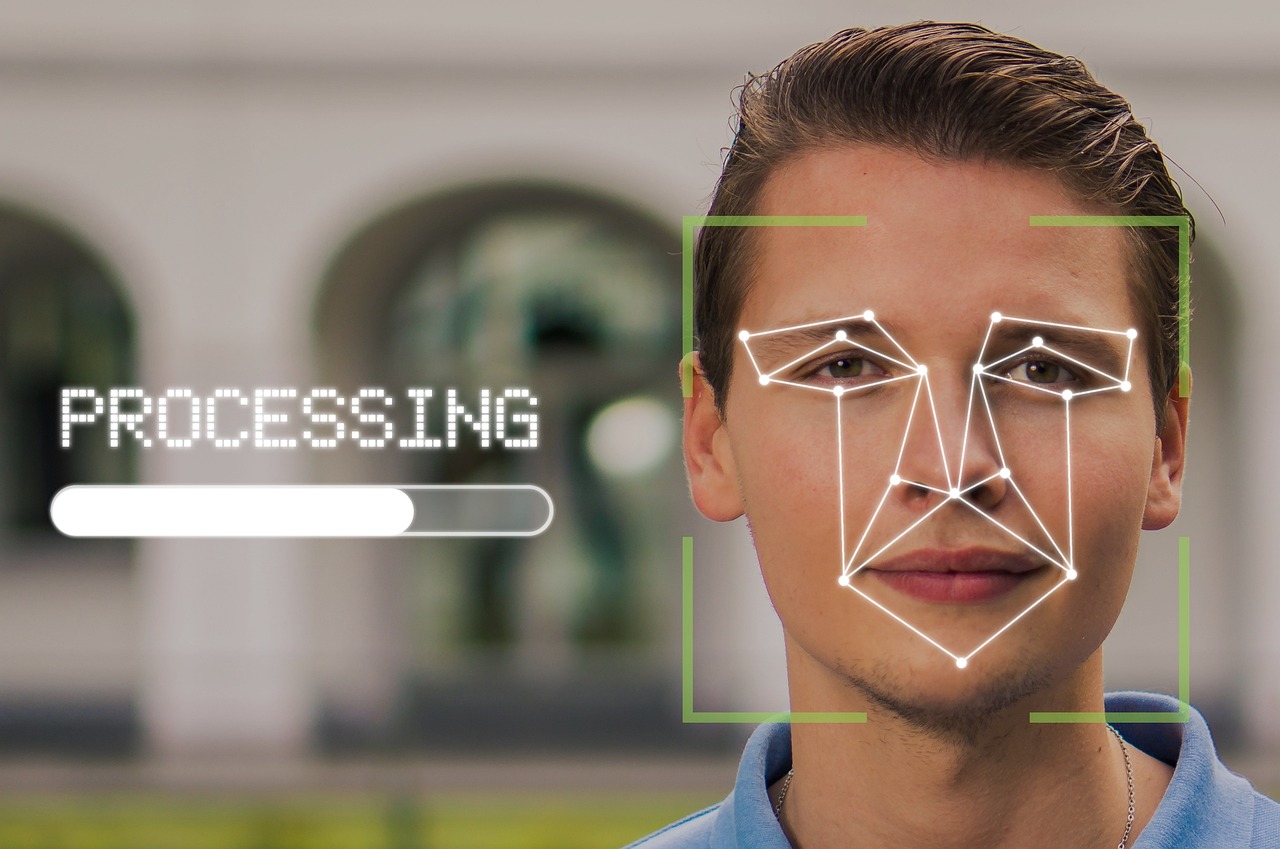
How Accurate Is Facial Recognition?
The Federal Bureau of Investigation (FBI) has run over 390,000 facial recognition searches since 2011. The Department of Homeland Security has also said it...
New Method For Scanning Hidden Weapons
A new scanning solution uses advanced sensors and artificial intelligence to detect a wide range of concealed weapons and threats, such as firearms, metallic...
Facial Recognition Technology Receives Backlash From Public
The US Department of Defense’s biometrics and identity tools are on track to support joint all-domain operations. But in order to accelerate the adoption...
Facial Recognition Technology is On The Rise For 2023
Facial recognition technology is increasingly used by US federal agencies - this is one of the insights of a new Government Accountability Office report....
Security Crisis: New Weapon Detection System Developed
Mass shootings have become a critical problem in the US. 611 mass shootings occurred in the US in 2020, a 47% increase from 2019,...
AI Offers Unbelievable Next-Gen Video Analytics
While artificial intelligence offers the power to drive a vast array of analytics solutions, many of the newest technology developments have been driven by...
Ghost Imaging – Capture Moving Objects With Light
An unconventional imaging method is known as ghost imaging. One of its advantages is that it allows one to form an image by illuminating...
Airport Security Reaches New Horizons
An airport passenger’s identity will be verified and he or she could move through security in about 6 to 10 seconds thanks to new...
Biometric Solution for Improving Security at Airport Staff Access Points
Airport operator Fraport recently launched its “Biometrics@Controllane” project to improve security at staff access control points using biometric solutions. Among the partners invited to...
Virtual Reality Advances Seaport Management
Virtual Reality can help cope with the massive work overload at seaports. New technology assists US Custom and Border Protection (CBP) employees in visualizing...
Will Doorbell Camera Survey Neighborhoods?
A series of 17 patents granted to Amazon for its Ring products over the last two years seems to suggest the company is working...
Self-Screen and Board
Passenger screening automation will create the next-generation screening experience at airports. A new program by the US Department of Homeland Security (DHS) Science and...
Perimeter Security at the Next Level
New intrusion detection technology offers a higher level of protection and false alarm immunity than traditional shock sensors, which often lack the ability to...
Business-Gov’t Collaboration in Search and Rescue Technology
The US Department of Homeland Security (DHS) is interested in new technologies in public safety, rescue response and more. The DHS issued a request...
Register Now to INNOTECH Cyber, HLS and Innovation Event
iHLS is proud to present INNOTECH 2021 - the International Cyber, Homeland Security Technologies and Innovation event. A giant two-day exhibition with national pavilions...
Interested in Cyber, HLS, and Innovation? Attend INNOTECH 2021 at EXPO...
iHLS is proud to present INNOTECH 2021 - the International Cyber, Homeland Security Technologies, and Innovation event. A giant two-day exhibition with national pavilions...
E-Commerce Giant’s Move Raises Concerns
While the idea of a contactless scanning of your palm print to pay for goods during a pandemic might seem like a good idea,...
New Kind of Security Checkup Tested in Airport
Seattle-Tacoma International Airport (SEA) is testing technologies to modernize the travel experience and help people stay safe during the COVID-19 pandemic.
SEA Spot Saver is...
Japan Enhances Security Towards Olympic Games
Towards the Tokyo Olympics in July, Japan is enhancing security measures in public transportation. The Transportation Ministry is pushing plans to give railway personnel...
5G Network to Accelerate Operations in Leading Int’l Airport
Various applications of the Internet of Things (IoT) in airports, automated vehicles on the runway and mobile security systems involve large quantities of data....