NASA Report on Unidentified Anomalous Phenomena Research
NASA announced it intends to take steps to understand unidentified anomalous phenomena (UAP, also referred to as UFO).
The space agency released mid-September the final...
Cyber Crisis Exercises in Critical Infrastructure and Operation Technology – in...
Written by Or Shalom
Cyber crisis exercises have many benefits for the organization. The exercise allows experiencing scenarios (sometimes under conditions of uncertainty) and affects...
Considerations in the Preparation and Implementation of Security Technologies in Olympic...
Written by Or Shalom
Preparations for the Olympics in France are at their peak, and so are the preparations in matters of security. The security...
Theoretical Physicist Calls AI Fears ‘Overblown’
Theoretical physicist Michio Kaku says that the public’s anxiety over new AI technology is misguided.
In an interview with CNN, Kaku said that chatbots will...
Seeing Is No Longer Believing – Is Generative AI Destroying The...
As Generative AI becomes more sophisticated, which is happening at top speed, it is important to ask: is Generative AI undermining the very foundation...
Global Trends and The Influence of R&D on the UAV Defense...
Article by Or Shalom
The use of UAVs for various missions has grown significantly in the past few years. In addition to their use in...
Godfather of AI Warns of Potential Dangers
The "Godfather of AI", Geoffrey Hinton, has quit his role at Google to allow him to speak more freely of the potential dangers in...
Are Employee Monitoring Tools Too Invasive?
A recent study reveals that million of US employers utilize invasive digital tracking tools to monitor their employees, and that number is only expected...
The Value of Data in Machine Learning
Data is highly valued in today's society. It can reveal previously unseen patters and behaviors, which can in turn offer insight into how things...
Used Smartphones Are Outselling New Models – Why?
The International Data Corporation (IDC) recently reported that new smartphone shipments had plummeted 11.3% to 1.21 billion units. By contrast, the global demand for...
3D Printing – The Building Blocks of The Future
3D printing promises to transform the way we live, and even where we live. James Rose, director of the Institute for Smart Structures in...
Cyber Security – Prevention First
As cyber criminals become more sophisticated with their attacks, we must shift from a detection and response approach to cyber security, to a prevention...
Why Should You Care About Cyber Threat Intelligence Sharing?
Cyber space has expanded beyond anyone's ability to navigate it safely on their own. The number of cyber threats put against organizations, companies and...
Should You Use A Password Manager?
While password managers are mostly considered safe to use and even often recommended as an efficient security tool and password storage, consider these following...
UK’s Online Safety Bill is Problematic – Lets Talk About That
UK's new online safety bill has passed both first and second reading in the house of the lords, and is close to becoming an...
The Most Important Innovation, According to Bill Gates
Bill Gates has spoken out about the most innovative technology in the market during a recent podcast with the German business site Handelsblatt. In...
Boston Marathon Bombing (2013) As a Case Study and Possible Insight...
By: Or Shalom, HLS expert
A decade has gone by since the Boston marathon bombing, and there is much insight that can be learnt by...
Researchers Predict That: Robots Will Take Over These 5 Workplaces
The advancements in technology and rise in developments of artificial intelligence, virtual reality systems and more are sure to have a massive impact on...
Have We Lost The Battle For Our Privacy?
It’s time to blow the whistle on a well-known secret shared among the cyber security researchers’ community: The digital world security has reached The...
What Happened to BlackBerry?
If we look back a decade ago, to the early 2010s, we would be able to see many adults and youths alike using the...
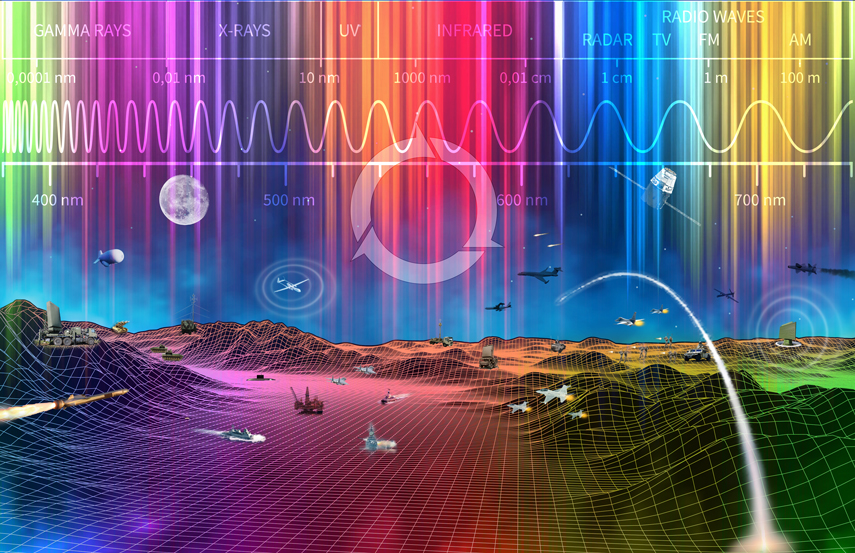
The Spectrum Management Challenge in the Modern Battlefield
The electromagnetic (EM) spectrum is used by a wide variety of systems, commonly referred to as "spectrum dependent systems" (SDSs). Each SDS may transmit...
Egozi: Russia to Control Syria
By Arie Egozi
Russia, in its efforts to gain full control of Syria, is operating one division of the Syrian army as part of the...