Digital Control Towers Will Not Be Located at Airports
Digital remote control towers are revolutionizing air traffic management. Digital air traffic control means airports can manage their planes from anywhere in the world....
Anti-Drone Weapons – Frequent Measure in Large Scale Events Security
The rise of drones has allowed new and creative ways to penetrate highly secure environments. This is the reason why anti-drone weapons are becoming...
Will Remote Identification be Compulsory for Drones?
Millions of the agile and affordable quadcopters and other drones have already been sold in the United States. Anonymity is already not an option...
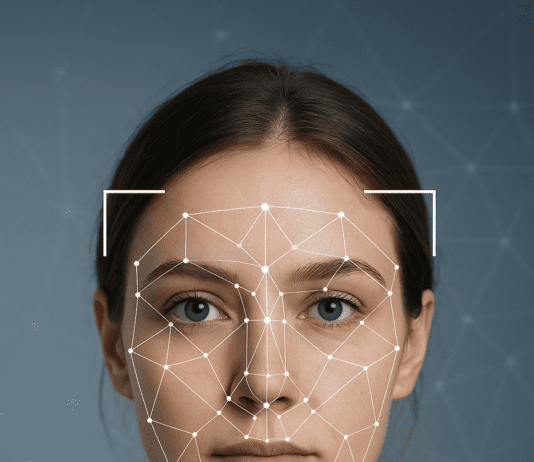
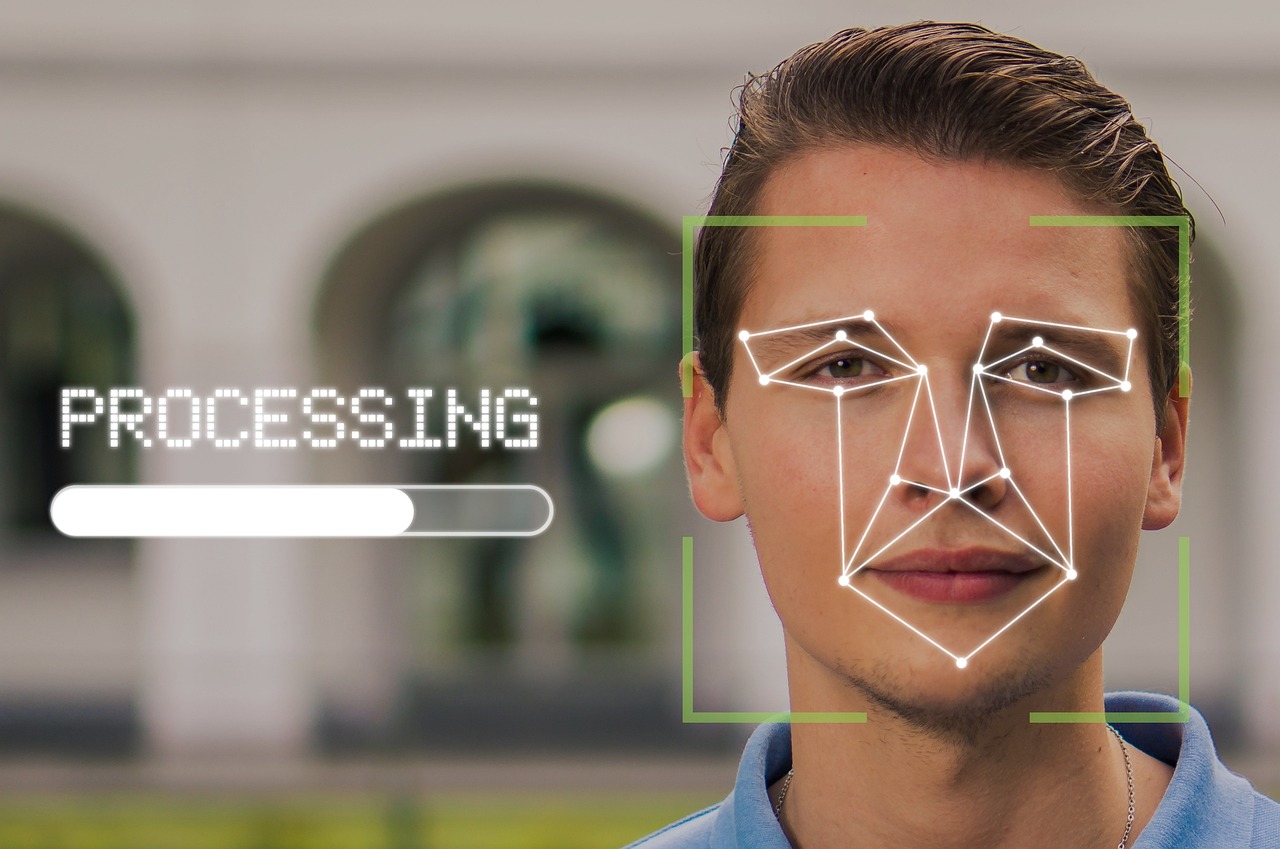
Several Biometric Technologies to be Merged to Improve Identification
The US biometric identification system is gaining momentum. The new Homeland Advanced Recognition Technology (HART) platform supports the Department of Homeland Security and its...
Risk Assessing Software to Accelerate Security Checks
With the overwhelming amount of data that has to be reviewed during border security checks, as well as limited budgets and resources in governments,...
Major Improvement Expected in Airport Security Queues
Going through airport security can be a nerve-wracking process. In the US, whether it’s adhering to Transportation Security Administration (TSA) rules of removing laptops...
Anti-Terror Barrier System Offers Smart-City Features
A new lightweight, temporary alternative to traditional barriers made from concrete or steel blocks was recently deployed to protect fans from vehicle-led terrorist attacks...
iHLS Accelerator is Looking for Game-Changing Technologies
We at the iHLS Security Accelerator are looking for disruptive ground-breaking technologies offering solutions for civilian defense, securing government institutions, vital infrastructure and borders,...
iHLS Accelerator Startup: Disruption in IoT Command and Control
The market of the IoT connected devices is in the midst of a major revolution which has already altered every field, from domestic devices,...
New Weapon Detection Solution Might Prevent Next Active Shooter Attack
New security tools are needed to prevent the types of mass shootings that have become endemic to US culture in recent years. With policymakers...
Smartphones May Not Be Allowed at US Military Installations
The US Defense Department is reviewing whether cellphones should be banned at the Pentagon - where 23,000 military and civilian personnel work at the...
New Tech to Detect Threats in Crowded Environments
Everyone wants to be safe and secure, but is it realistic to perform in crowded environments such as a metro station security screening like...
Video Systems, Less Familiar Target of Cyber Threats
By Dorit Guterman, Ledico Security Systems, Tomer Nuri, Team
Information and cyber security events can occur also via security cameras and other IoT devices. As result,...
“High Tech Policemen” Will Protect Upcoming Olympics
The Winter Olympics will take place in South Korea during February, and the country is planning to deploy 10,000 police officers in and around...
Drone Ballistic Parachute Recovery System To Hit Market Soon
Civilian drones have become a big part of many companies lives, from filming movies and advertisements to delivering packages like Amazon wants to start...
What is Threatening Military Installations?
There are growing concerns in the US that terrorists and spies could use remotely piloted unmanned aircraft for surveillance, espionage and attacks, from monitoring...
Israel Establishes National Task Force for Drone Security Regulation
The growing use of cheap and accessible commercial drones and the involvement of terrorist and criminal actors have been increasing the threat to security...
Mimicking Falcons in Next Generation Drone Defense
Next-generation drones, built to track and hunt other drones, might be designed using hunting principles used by one of nature's most capable predators. Researchers...
Expect Resurgence in Video Analytics in 2018
An increasing interest in video analytics was demonstrated in 2017 from commercial industries using the technology for business operations, yet the security industry remains...
U.S. CBP to Become Much More Effective With Common Viewer System
Customs officers are the front line of enforcing lawful and secure trade, screening for illegal contraband and dangerous goods. Their challenge is to quickly...
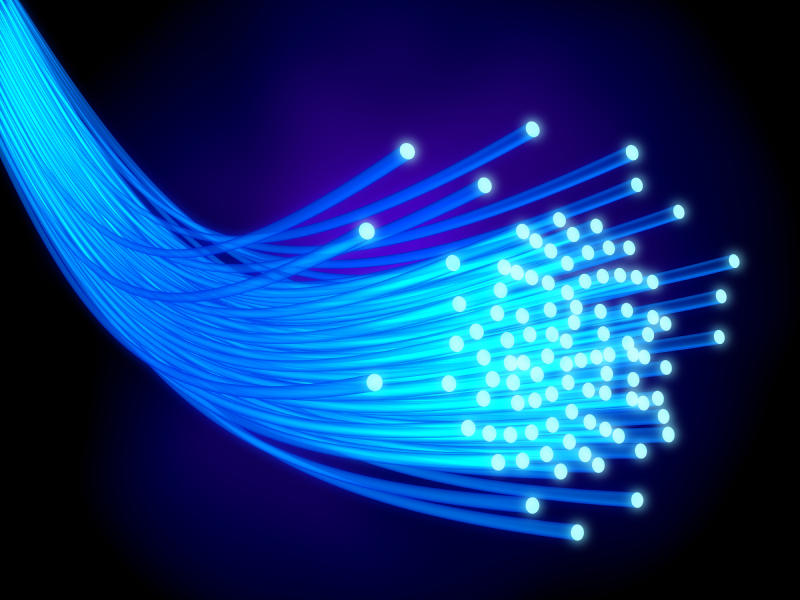
Railway Detection via Optic Fibre Technology
Various security monitoring applications used in the rail industry require individual systems, creating expensive and complex integrations for surveillance centres. Moreover, installations tend to...
AI Makes Traveling More Secure
Artificial intelligence technology is infiltrating the travel industry, and it’s bringing a host of new conveniences and capabilities with it, from personalized recommendations and...