ISIS is becoming more deadly by using chemical weapons
It was only a matter of time.
Kurdish sources in Iraq have said they have evidence that the Islamic State (ISIS) used chlorine gas as...
DNA synthesis may pose a risk of resurrecting deadly viruses for...
Homemade deadly viruses?
Scientists are warning that decades of public research on the sequencing of virus DNA are now posing unforeseen threats, as synthesis technologies...
International cyber terror: Lizard Squad strikes back
The hacking group known as Lizard Squad has been making quite a nuisance of itself, associating the hackers with two high profile events. Lizrad...
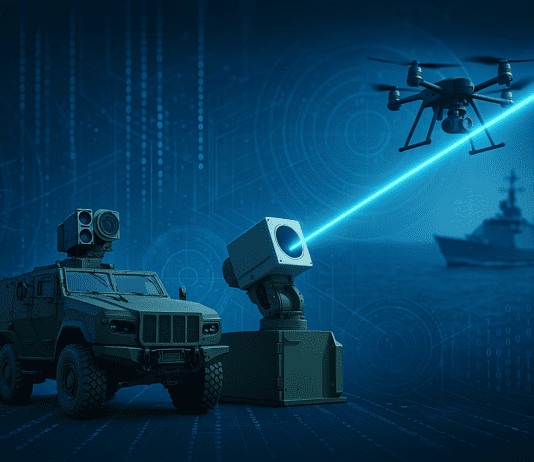
The U.S Secret Service may exercise drone defense
The threat in clear an imminent. In an effort to prevent attacks or surveillance by Unmanned Aerial Vehicles (UAV), the Secret Service issued a...
UK Announces Creation of the 77th Cyber warfare Battalion
Britain’s cyber unit for soldiers familiar with social media.
Documents leaked by Edward Snowden demonstrate that the NSA and its allies are preparing for future...
Terrorists plan to attack rail systems
Has Successful Terror Gone to Ground?
Terrorists have shifted their focus in recent years away from attacking airlines to attacking subway and rail systems. This,...
Are Outdated Intelligence Tactics Allowing the UK Terror Threat to Grow?
Britain’s intelligence agencies are leaving known terrorists to “carry out evil deeds” through a flawed approach which focuses on disrupting suspects rather than prosecuting...
iHLS TV Weekly Video Report – March 17th 2015
Register to iHLS Israel Homeland Security
In this weekly Video report (March 17th 2015):
Converted Prop Guns Are Assassins’ Weapon of Choice
Robot Firefighter Puts Out Its...
Terrorism challenge is big and growing
Threats from terrorism will continue to challenge the United States. This, according to U.S. counterterrorism analysts
In a recent congressional testimony, James Clapper, Director of...
The danger of Cyber attack on civil aviation is sky high
The aviation industry is slow in responding to the threat posed by cyber criminality. This, whether it is posed by criminals, terrorists, nation states,...
Pakistan successfully tests missile launching drone
Pakistan’s Army announced the country has recently made a successful launch of a laser-guided missile from an indigenously-developed armed drone, or UAV (unmanned aerial...
Barak-8 missile on the way to full operability
The Barak-8 is one of the most advanced air defense systems in the world today. A source in the program told i-HLS the system...
Dramatic Improvement in Intelligence Sharing Because of ISIS
European countries are voluntarily providing the United States with large amounts of information about their citizens. Data transfers focus in particular on citizens attempting...
Terrorism and the U.S – The Enemy within?
U.S. security officials have long considered sovereign citizen groups a growing threat to domestic security. In a 2014 survey of state and local law...
Supporters of Islamic State have at least 46,000 Twitter accounts
Supporters of the terrorist group, Islamic State of Syria and Iraq, popularly known as ISIS, used at least 46,000 Twitter accounts from September through...
Britain’s nuclear reactors vulnerable to terrorist drone attacks
This danger is imminent. Britain’s aging nuclear power plants are vulnerable to terrorist attacks by unmanned drones that could kill thousands of people. This...
The Growing club of armored cars users
Australian Prime Minister Tony Abbott has recently started using his new armored BMW as his regular mode of transportation. Abbott treated himself to the...
NSA Surveillance Software Infecting Thousands of Computers Worldwide
A sophisticated spying campaign infected tens of thousands of computers worldwide with surveillance software, some embedded in hard drives, according to a report from...
Two names – one terror organization
Nigeria’s Islamist group Boko Haram has declared its allegiance to Islamic State. In a video posted online, Boko Haram’s leader, Abubakar Shekau, in an...
Cyberespionage tactics
Kaspersky Lab reveals latest cyberespionage tactics: complexity and modularity VS functionality.
Nation-state sponsored cyberespionage attacks are becoming more sophisticated, targeting carefully defined users with complex,...
Counterterrorism laws in Europe outdated
As though anyone still entertained any doubts, Europe’s counterterrorism laws cannot deal with the current situation where terror groups are flooding the continent. This...
iHLS TV Weekly Video Report – March 10th 2015
Register to iHLS Israel Homeland Security
In this weekly Video report (March 10th 2015):
Cyber in the IDF: Warfare and Security
Terrorism Finance: Experts Worry ISIS Already...