Why Cybersecurity Works Better When Defenders Share Data
Organizations are increasingly expected to share data across corporate boundaries, yet cybersecurity risks have never been higher. As partnerships, mergers, and joint technology projects...
The Wind System Designed to Be Deployed Fast — and Almost...
The rapid growth of artificial intelligence is reshaping energy demand in ways few power systems were designed to handle. Large-scale data centers now consume...
Why Future Minehunting May Happen From Shore, Not at Sea
Naval mines continue to pose a disproportionate threat to modern fleets. Relatively cheap to deploy and difficult to detect, they can deny access to...
Not Just Fast — This Missile Knows How to Evade
Defending maritime approaches has become increasingly complex as naval air defenses grow more capable. Modern surface combatants rely on layered sensors, radar-guided interceptors, and...
This Fiber Trick Could Simplify Secure Laser Links in the Sky
Laser-based data links are increasingly attractive for aircraft and space systems that need to move large volumes of information quickly. Free-space optical communication (FSOC)...
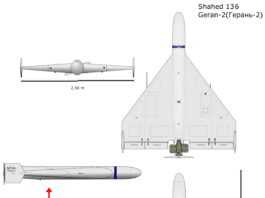
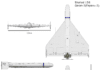
A Missile Meant for Tanks Just Took Down a Drone
A growing challenge for modern forces is the rapid spread of unmanned threats across air and maritime domains. Small drones and unmanned surface vessels...
AI Firewall Unveiled: Is Your Network Finally Unhackable?
aiFWall Inc. unveiled an innovative solution for securing artificial intelligence systems. It is a dedicated firewall designed to protect enterprise AI deployments by using...
A Militay Gamechanger: AI-Powered AR Goggles for Armored Vehicles
Finnish startup Distance Technologies has unveiled its Field Operator HUD (FOH), an innovative augmented reality (AR) system for combat vehicles. The system, which has...
How Visible Light Could Power Secure, Jam-Resistant Links
Wireless communication is becoming increasingly crowded. Radio-based links are under constant pressure from spectrum congestion, interference, and regulatory limits—challenges that are especially acute in...
How Active Protection Is Redefining Tank Survivability
Modern armored warfare is being reshaped by the rapid spread of advanced anti-tank weapons. Guided missiles, top-attack munitions, and portable rockets are now widely...
The Radar Plane That Survived the Budget Axe
Airborne early warning remains one of the most difficult capabilities to replace. Modern air combat depends on long-range detection, tracking, and battle management, yet...
Cybercrime’s New Wave: Has AI Made Attacks Unstoppable?
Cybercrime is entering a phase where speed and scale are no longer limited by human skill. For years, defenders have tracked the evolution of...
Young Startups Drive Defense Innovation: An Unusually High Volume of Orders...
In recent years, the defense establishment has been facing a dual challenge. On the one hand, there is a growing need for fast, flexible...
Learn From Their Mistakes: The Pentagon’s AI Blunder
The Pentagon recently embarked on an ambitious journey to implement artificial intelligence (AI) tools across logistics, maintenance, and intelligence functions. Expectations were high: AI...
This Disposable Decoy Lures Missiles Away from the Real Aircraft
Modern combat aircraft face a steadily evolving threat environment. Radar-guided missiles launched from both air and ground platforms are becoming faster, smarter, and better...
A Missile Launcher That Crab-Walks and Leaves No Heat Trail
Moving extremely heavy military payloads has always involved trade-offs. Conventional missile launch vehicles rely on large diesel engines, rigid axles, and complex mechanical linkages....
How “Full-Stack” Cities Could Reshape Modern Warfare
Advanced military systems increasingly depend on civilian technologies that scale fast, iterate quickly, and draw on dense supply chains. Drones, electric propulsion, sensors, and...
Maduro’s Capture: The Invisible Weapon That May Have Ended the Fight...
Stories of invisible weapons tend to surface after fast, asymmetric operations. When defenders are overwhelmed quickly, especially by a smaller force, the search for...
This Uncrewed Helicopter Could Hunt Submarines for Hours
Operating helicopters in the North Atlantic has always carried high risk. Harsh weather, long distances, and the growing presence of submarines make maritime aviation...
SpaceX’s Secret Launch: New Spy-Sat Tech Unveiled?
Modern intelligence collection is facing a structural problem. Traditional spy satellites are powerful but scarce, expensive, and vulnerable. With only a handful in orbit,...
The Battle Tank Built Around Sensors, Not Just Armor
Heavy armored warfare is entering a transition period. Legacy main battle tanks remain lethal, but they are increasingly challenged by precision anti-tank weapons, drones,...
Fighting Drones from Space: A New Defense Concept Emerges
As drone threats grow in range, speed, and sophistication, many existing counter-UAS systems struggle to keep up. Ground-based radars are limited by terrain, jammers...