WhatsApp Tests Usernames for Number-Free Messaging
WhatsApp is preparing to introduce a long-requested feature: usernames. According to details uncovered by WABetaInfo, WhatsApp is testing a new feature that would allow...
New Cyber Command to Lead AI-Enhanced Digital Combat Operations
The United Kingdom has unveiled a major investment in digital warfare capabilities, committing over £1 billion ($1.3 billion) to establish a new cyber command...
Chinese Hackers Exploit Google Calendar in Unprecedented Cyber Espionage Campaign
A new report reveals that Chinese state-backed hacking group APT41 has developed a novel method to conduct cyber-espionage by exploiting Google Calendar as a...
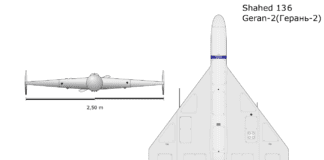
Are Russia’s UAVs Controlled via Telegram?
A recent report by The Economist suggested that newer variants of the Iranian-designed Shahed UAVs, commonly used by Russia in its war with Ukraine,...
Chrome Introduces One-Click Fix for Leaked Passwords
Google Chrome has rolled out a security enhancement that allows its built-in Password Manager to automatically replace compromised passwords, offering users a seamless way...
Russian Cyber Campaign Targets Western Military Aid Logistics to Ukraine
In a covert effort to interfere with military support flowing to Ukraine, Russian state-sponsored hackers have been systematically targeting critical defense and transport infrastructure...
Anthropic’s New Claude AI Raises the Bar for Code Generation—And Red...
Anthropic has unveiled its latest generation of Claude AI models, claiming a major leap forward in code generation and reasoning capabilities while acknowledging the...
TeleMessage Hack Also Exposes U.S. Government Officials’ Metadata
A recent cyber breach involving the government-grade messaging platform TeleMessage has revealed that dozens of U.S. federal officials were unknowingly swept up in the...
Phishing Tactics Are Evolving—Here’s How Cybercriminals Are Getting Smarter
Phishing remains the most frequently reported cybercrime in the United States, with over 193,000 incidents recorded by the FBI in the past year. While...
Cybercriminals’ New Favorite AI Tool
A new artificial intelligence chatbot, Venice.ai, is attracting attention for all the wrong reasons. Designed to function without the ethical restrictions found in mainstream...
Undocumented Communication Devices Found in Chinese Solar Tech Spark U.S. Security...
A recent investigation has uncovered troubling vulnerabilities in Chinese-manufactured solar technology widely deployed across the United States. According to findings reported by Reuters, hidden...
TikTok Faces EU Scrutiny Over Advertising Transparency
The European Commission has issued preliminary findings that suggest TikTok is failing to meet critical transparency requirements under the Digital Services Act (DSA), specifically...
OpenAI’s Vision: A Hyper-Personal AI Assistant That Remembers Everything About You
OpenAI is moving toward a bold new direction in AI personalization—envisioning a model that can retain and reason over a person’s entire digital footprint....
FBI Warns of AI-Powered Voice Scams Impersonating U.S. Officials
In a recent public alert, the FBI has flagged a concerning wave of cyber activity involving AI-generated content used to impersonate high-ranking U.S. government...
DDoS Attacks Target Swiss Websites Amid Eurovision Festivities
As the Eurovision Song Contest draws global attention, Swiss cybersecurity authorities have reported a series of distributed denial-of-service (DDoS) attacks aimed at local websites...
Massive Data Leak Exposes Sensitive Job Seeker Information on Recruitment Platform
A significant data breach has been uncovered involving HireClick, a recruitment platform catering to small and mid-sized businesses. The leak, which was first detected...
The Emerging Threat of Autonomous AI-Powered Cybercriminals
As artificial intelligence (AI) technologies become more advanced, experts warn of an imminent shift in cybercrime, with AI-driven attackers becoming a major threat to...
North Korean Hackers Target Ukraine to Gauge Russian Military Needs
New findings reveal that North Korean state-sponsored hackers are conducting cyber-espionage operations against Ukrainian government institutions and affiliated organizations. But the objective is strategic...
iOS Game Exposes Hundreds of Thousands of Users to Serious Data...
A mobile game on Apple’s App Store has left hundreds of thousands of users exposed to serious privacy risks, after researchers discovered that the...
North Korean Hacker Group Adapts Remote Work Fraud Tactics
New research reveals that the North Korean cyber group known as Nickel Tapestry is evolving its remote work deception tactics, expanding beyond U.S. companies...
Chrome Adds On-Device AI to Detect Scams in Real Time
Google is rolling out new anti-scam capabilities in its Chrome browser, introducing a lightweight on-device AI model designed to spot fraudulent websites and alert...
FBI Warns: Old Routers Exploited in Cybercrime Proxy Networks
The FBI has issued a security alert warning that aging home routers, particularly discontinued models from Linksys, are being exploited by cybercriminals to conceal...