New SIGINT Prototype Aims to Keep Units Connected When Signals Disappear
Modern military operations depend on uninterrupted communication and rapid data sharing, yet many battlefields are anything but cooperative. Urban density, electronic warfare, and natural...
When Fighters Retire, Some Come Back as Target Drones
Modern air forces face a growing challenge in evaluating new air-to-air weapons: missiles must be tested against maneuvering, fighter-size targets, not simulators or scaled-down...
This Locally-Manufactured Wheeled Howitzer Brings Automation to the Front Line
For decades, Israel’s artillery relied on tracked systems introduced in the 1980s. While dependable, those platforms were manpower-heavy, slower to reposition, and increasingly mismatched...
Engineers Flip the Script with a Reverse-Engineered Drone
Modern militaries face a growing challenge: traditional unmanned aircraft such as MALE-class drones offer advanced ISR and strike capabilities, but their high cost and...
The Counter-UAS Platform That Connects Everything in Real Time
The rapid spread of unmanned aerial systems has made airspace security more complex for military forces and critical facilities. Small drones are increasingly capable,...
A Stealthy FPV Drone With Zero RF Signal? Yes, It Exists
Modern FPV drones have proven valuable for reconnaissance and precision attack roles, but their dependence on radio links has become an increasingly serious limitation....
The Shape-Shifting “Octo Robot” Built for Stealth
Robots intended for complex natural environments face a familiar problem: rigid bodies and fixed-color surfaces make them easy to detect and limit their ability...
An AI-Powered Shield Designed for the Drone-Swarm Era
The rapid spread of small, inexpensive drones has created a growing challenge for security forces and militaries alike. What were once isolated aerial threats...
The Invisible Hand: How Drones and Lasers Are Rewriting the Rules...
Forget the battlefields of old. A silent, rapid transformation is underway, fundamentally altering the calculus of conflict and ushering in an era where speed,...
An Air Defense Deal Marks Another Step in Israel’s Defense Exports
As aerial threats become more diverse and harder to detect, many countries are reassessing how well their air defenses can cope with modern risks....
A New Mine-Clearing System That Turns Dangerous Ground Into Passable Terrain
Minefields remain one of the most time-consuming and dangerous obstacles for ground forces. Traditional breaching tools—mechanical rollers, plows, and manual clearing—can take hours, require...
The Fighter Helmet That Replaces Night-Vision Goggles Entirely
Modern fighter operations place growing cognitive and physical demands on pilots. High-speed engagements, dense sensor inputs, and operations at night or in poor weather...
A New Foldable Drone is Built for Long Flights and Fast...
Border surveillance and wide-area monitoring often require small unmanned aircraft that can stay airborne for extended periods, carry multiple sensor types, and operate reliably...
A New Class of Drone Carrier Takes Shape
Modern amphibious forces increasingly rely on unmanned systems for reconnaissance, strike missions, and real-time situational awareness. Traditional helicopter assault ships are limited in the...
Seeing in the Dark: Cameras Get Snake-Like 4K Vision
High-performance infrared imaging normally requires exotic materials or cryogenic cooling, making it too costly for widespread commercial or security use. Conventional CMOS sensors—the same...
A Drone Just Proved It Can Outshoot a Jet
One of the biggest challenges in modern air combat is detecting, tracking, and engaging fast-moving aerial targets at long distances. Traditionally, only crewed fighter...
Underwater Drones Built for Months-Long Patrols
Modern naval forces face a persistent challenge: how to monitor vast stretches of ocean without relying on crewed submarines or costly patrol cycles. Underwater...
Stopping the Domino Effect: Rethinking Cyber Resilience
Modern infrastructure is increasingly dependent on tightly connected digital systems. Power grids, transport networks, hospitals, and communication platforms all rely on data flows that...
This Huge Jet Drone Doesn’t Just Fly—It Brings Backup
Modern air defenses are increasingly challenged by the growing use of unmanned aircraft, but the rapid evolution of drone swarming threatens to complicate this...
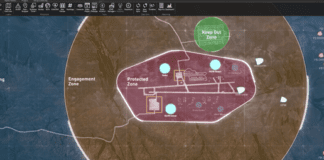
T-Dome: A Smarter Shield Integrating Air, Missile, and Drone Defenses
Modern air-defense systems face a common problem: sensors, interceptors, and command centers often operate in parallel rather than as a synchronized whole. This slows...
This Armored Monster Just Got a High-Tech Boost
Armored fighting vehicles are expected to operate in increasingly complex environments, from dense urban terrain to wide-open maneuver corridors. They must withstand emerging anti-armor...
A Billion Reasons Investors Are Betting on Israeli Defense Tech
Israel’s security landscape has increasingly depended on rapid technological adaptation, but until recently, defense-focused startups struggled to attract significant investment. The year 2025 marks...